Most of the viruses modify the attributes of a file or a folder such that they become very hard to access. Some of the attributes that are changed in a file or a folder are the read, write or the execute permission on that file. Using ‘attrib’, one of the cmd commands, we can try our hands to change the attributes of a file and reset the file’s internal structure in order to recover a file.
How is a virus different from any other file on Windows? A virus can be present in your system as a file format which has the following properties:
- A virus can be a file hidden from a user
- A virus can be present in the form of an ‘autorun’ or ‘Autoexec’ file
- A virus can be an exec file
- A virus can be a file with different attribute permissions
Some of the well-known examples of the above kinds of the viruses are:
- Autorun.inf
- Ravmon.exe
- New Folder.exe
- svchost.exe
- Heap41a
Remove Virus Using CMD from USB/ any Drive on Windows 10:
In order to remove a virus using cmd, we will use a famous cmd command called ‘attrib‘ command.
It can be easily guessed from its name that the ‘attrib’ command represents different attributes of a file, folder or a directory. This command is mainly responsible for displaying, setting and removing the different attributes like read-only, archive, system, and hidden attributes of a file or folder.
Using this command, we will try to change the attributes assigned to a file and thus recover our file.
Here are the basic attributes of the ‘attrib’ command which we will use later:
- R – R represents the “Read-only” attribute of a file or folder. Read-only means the file cannot be written or executed.
- H – H stands for the “Hidden” attribute.
- A – Similarily, A stands for “Archiving” which prepares a file for archiving and,
- S – S attribute changes the selected files or folders into a system file from a user file by assigning the “System” attribute to that particular file.
“attrib” Syntax:
ATTRIB [+ attribute | – attribute] [pathname] [/S [/D]]
In the above command, let’s see what the different parameters and switches are:
‘+ / –’ : To enact or to cancel the specified attribute.
‘attribute’ : As explained above
‘/S‘ : Searching throughout the entire path including subfolders
‘/D’ : Include any process folder
‘pathname’ : Path where the target file or folder is located.
Here is the proper syntax for attrib command:
ATTRIB [+R | -R] [+A | -A ] [+S | -S] [+H | -H] [+I | -I] [drive:][path][filename] [/S [/D] [/L]]
Let’s get started:
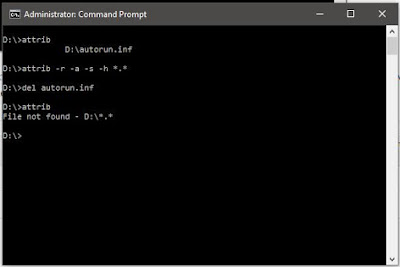
I am going to transfer an ‘autorun.inf‘ virus from my USB drive to my D: drive and delete that virus from my D: drive.
- Run command prompt as an administrator
- Since the autorun.inf virus is in my D: drive, I am going to change the drive to D: drive. It can be done by typing D: and press enter.
- type attrib and press enter. This command will list out all the files inside the current drive and you can clearly see the autorun.info virus listed below.
- To remove Virus using CMD, type into your command prompt attrib -r -a -s -h *.* and press Enter. This will remove the Read Only, Archive, System and hidden file attribute from all the files.
- -r is for removing the read-only files
- -a is for removing the archive file
- -s is for removing the system file
- -h is for removing the hidden file
- *.* for all the files with all different types of file extensions\\
- Note that this command will only remove the different attributes from different files. However, the files will still be there. Now time has come to delete the virus. So, to delete the virus, type del autorun.inf and enter
- Once you have pressed enter, that file should get deleted from the current drive. In case, you want to delete that file from a USB stick, then you can change your current drive to USB drive current drive in step 2 and follow the commands.
- You can again type ‘attrib’ command to see if the deleted file exists or not. As seen above, it does not exist anymore in the D drive.
- To remove other viruses with extensions such as ‘.ink’, ‘.exe’, just type Del *.ink or Del *.exe respectively to delete those suspicious files.
I hope this would have been informative for you. If you know some other tricks, let us know in the comments below.

























birkin bag
ReplyDeletesupreme outlet
moncler
yeezy shoes
kyrie 6
yeezys
supreme hoodie
yeezy
longchamp handbags
yeezy shoes